Recent Strong User Authentication Adoption
Failure of authentication can lead to significant impact for consumers, business, and government. Despite the recommended solution of multi-factor authentication being available for close to two decades adoption rates have lagged. This lag has contributed to attackers being able to compromise critical systems through the reuse of basic techniques. Support for deployed solutions, user perception of usability gaps and lack of general understanding as to the risks involved are all argued as contributing towards this lag. Additionally, lack of understanding around what ‘good’ constitutes around strong authentication and how to deploy it is also an issue. This paper will provide research-based guidance on what strong authentication is and what lessons have been learnt from deploying it. The paper will also provide a view of what strong authentication technologies are available in the wider market for use. The material can then be used either as basis for subsequent research or to support the deployment of strong authentication across multiple areas.
Introduction
Authentication is the process of verifying the identity offered by a subject (Dasgupta et al., 2017). Three traditional methods are for authentication are taught: knowledge (i.e. knowing a password), inherence (i.e. fingerprint, face scan) and possession (i.e. security token) (Shah & Kanhere, 2019). A successful attack against the authentication process can allow an unauthorised party to assume the identity of a target.
Use of only knowledge-based authentication is regarded as weak. It can be broken by a brute force search (Wang et al., 2020), can be obtained using malware (Agrawal, 2020) or can be inadvertently disclosed. Additionally, management of knowledge-based authentication material (i.e., ‘passwords’) is seen as complex. Forcing users to complete complex tasks can lead to poor decisions being made (Theofanos, 2020).
The authentication process can be strengthened via several approaches. The main one of these is the use of multi-factor authentication. This is where authentication is done using a combination of factors. Deployment of multi factor authentication is recommended by multiple parties as a key step in improving security posture (Cyber Essentials | CISA, n.d.) (Essential Eight Explained | Cyber.Gov.Au, n.d., p. 8).
Despite the recommendations for implementing multi factor authentication and advantages if offers adoption across multiple sectors is understood to be slow (Frazier, 2019) (Manning, 2020). This is understood to have contributed to ongoing security breaches (The Breaches Multifactor Authentication Could Have Prevented | Tyntec, n.d.) (Verizon, 2020)
This paper provides an overall view of what is regarded as ‘strong authentication’, what lessons have been learnt from deploying it to date and what is available in the public market. From there conclusions can be drawn as to why it is not more widely available and deployed.
Methods
To determine a definition of strong authentication a review of recent published literature has been done. Goal of the review was to identify key concepts required for authentication to be regarded as strong. As part of the review limitations in current strong authentication systems was also looked at.
A desktop study was done which identified strong authentication options available to users in the current global market. As part of the study any formal vendor document on strong authentication availability or adoption was reviewed. Market study was limited in two areas. First only the top 25 websites listed in the Alexa Global top 500 sites (Alexa - Top Sites, n.d.) as at 16th of January 2020 were reviewed. For each website, a list of supported identities was gathered. Strong authentication options for those identities were analysed. Second is a review of strong authentication offerings in the current version of Windows, macOS, iOS & Android operating systems.
Data gathered from each category was summarised to understand availability of authentication technologies available in the wider market.
To gather lessons from adoption of strong authentication a review of recent published documentation was done. This will cover both journal literature and vendor documentation. Goal is to understand what technologies were deployed, why and what the lessons arising from the deployment were.
Results
Strong Authentication Concepts
Authentication is the process of verifying the identity offered by a subject (Dasgupta et al., 2017). Three separate methods (or ‘factors’) for authentication are understood: knowledge (i.e. knowing a password), inherence (i.e. fingerprint, face scan) and possession (i.e. security token) (Shah & Kanhere, 2019). A successful attack against the authentication process can allow an unauthorised party to assume the identity of a target.
Based on a review of available literature several key concepts are noted regarding strong authentication.
Attackers will attempt multiple techniques (Bonneau et al., 2012) when attempting to bypass authentication. This can include phishing, observation, guessing, theft, and impersonation. People attempting to attack the system can range from opportunists to organised crime to government sponsored operatives (Giandomenico, 2017). Sophistication of the attacks used will be in line with what a system is protecting against. Approach taken to authentication needs to allow for mitigating these threats.
As authentication is not the goal of a business process completing it needs to be as painless as possible (Schaffer, 2019). Goal is for the process to be effortless to use (Bonneau et al., 2012) while providing the appropriate outcome. To achieve this an understanding of the environment used to complete the authentication is required. Making a process difficult to complete will lead to users making poor decisions (Theofanos, 2020).
Multi-factor authentication is where two or more factors of authentication are used. It is a common recommendation for improving security (Essential Eight Explained | Cyber.Gov.Au, n.d.) (Cyber Essentials | CISA, n.d.). It strengthens the authentication process through using defence in depth (Sinigaglia et al., 2020) (Henricks & Kettani, 2019). To be successful at bypassing multi factor authentication an attacker must successfully compromise multiple components.
Protection offered by authentication is limited to when it occurs and what information it utilises. Authentication that only occurs at a single point in time will not provide ongoing protection (Shah & Kanhere, 2019). For example, once a phone is unlocked an attacker can access most of the content on it. To address this continuous authentication (Rocha et al., 2021) is needed. This revalidates the user identity through regular reauthentication.
In a similar fashion authentication that only references supplied material is weaker than one which considers available telemetry. As an example, a user may normally login to a website from Australia using a specific browser. An authentication system can examine this contextual data (Wiefling et al., 2020) and modify its behaviour appropriately (Arias-Cabarcos et al., 2019). As an example, the same user identity attempt to login from a different country using a different browser can trigger an alternative response. This can be further strengthened by considering the value of what a user is attempting to access. When access to a high-value asset is attempted the authentication system can apply additional levels of control. This is regarding as adaptive (Arias-Cabarcos et al., 2019) or risk based authentication.
Limitations with current strong authentication approaches
Strong authentication systems have been available for some time. The request for comment (RFC) describing HMAC-based One-time Password algorithm is dated 2005 (M’Raihi et al., 2005). Early patents describing this style of system were issued prior to that (Blonder et al., 1998). Despite the length of time it has been available adoption rates are noted as slow (Frazier, 2019) (Manning, 2020). A review of available literature identifies several potential causes.
In the first instance strong authentication solutions must be made available by a supplier. Users cannot adopt something which isn’t there.
Adoption of strong authentication is either by choice or mandate. Unless a user is made to adopt strong authentication by a supplier it is something they must opt into. For users to opt in they must be aware of the risks and understand how strong authentication can help address them (Ackerman, 2017). They also must be willing to accept the inconvenience imposed by the solution (Gupta, 2017). Perceived inconvenience of the solution will vary depending on the users accessing it (Das et al., 2019), task being completed and level of effort required.
Strong authentication solutions require access to additional technologies (De Cristofaro et al., 2013). For example, inherence-based authentication requires some form of scanner, possession-based authentication can require something to read tokens. Lack of user access to this type of technology means the user cannot access it.
Market Review of Strong authentication offerings
Review of Top 25 Websites
A review of the top 25 websites accessed from Australia as described by Alexa.com was done on the 16th of January 2020. Each of the websites offered functionality for a user to register an identity. The below table lists the identities supported on each website.
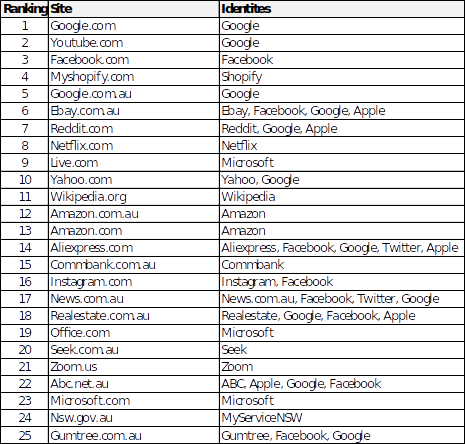
Listed identities identified were analysed to determine availability of multi-factor authentication options. Each of the identities support use of knowledge based single factor authentication. Availability of multi-factor authentication is mixed. Where multi-factor authentication is supported, none of the identities mandated its use as part of account signup. Some identities (Google, Microsoft) recommended its enablement. A summary of these results is shown in the below table.
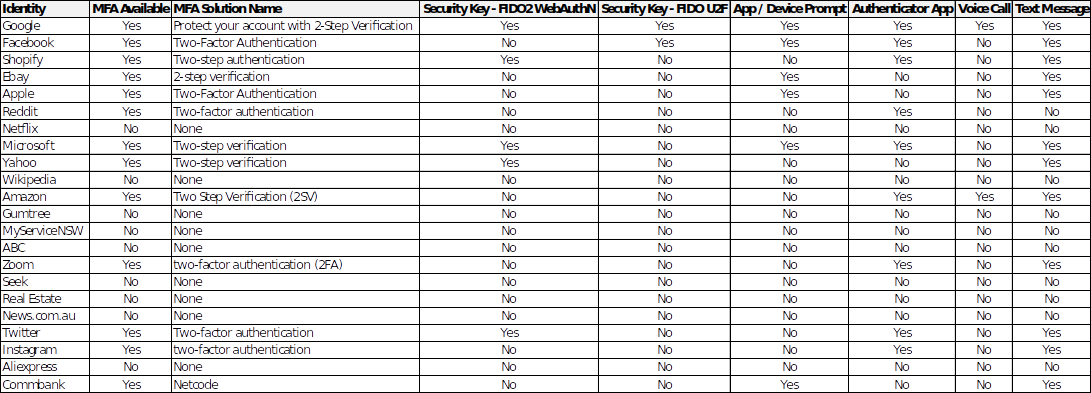
Second factor authentication options listed are:
- FIDO2/WebAuthN: Website has support for authenticating via WebAuthN. This allows users to authenticate using cryptographically based credentials stored in commonly available devices across both mobile and desktop environment. (FIDO Alliance, 2020)
- FIDO/U2F: Site has support for authenticating via Universal Second Factor (U2F). This technology is a precursor to FIDO2.
- Application or device prompt: Site has support for sending a prompt to an application or device controlled by the user. This allows the user to approve the sign-in separate to the existing login process.
- Authenticator app: Site has support for the user registering an authenticator application. The application then will then provide a code the user can utilise as a second factor. This will either use Time-based One-time Password Algorithm (TOTP), HMAC-based One-time Password algorithm (HOTP) or a propriety vendor-based solution.
- Voice Call: Site will provide the second material via a voice call. The material provided is normally a short code.
- Text Message: Site will provide the second factor material via a text message. The material provided is normally a short code.
Review of popular operating systems
Popular operating systems were reviewed to understand the availability of strong authentication. Systems reviewed were the current versions of Windows, macOS, iOS & Android.
Windows: Strong authentication is provided by the Windows Hello system (Microsoft, 2020). This allows for replacing passwords with a combination of PIN, biometric factor, or security key. Users are prompted to enable this at time of computer setup and after major system updates. Windows Hello can be used by consumers. It also allows for business use through supporting integration with enterprise architectures. Home users can also use their Microsoft identity as part of logging into Windows. This allows the operating system to leverage strong authentication features from that identity.
macOS: Two main authentication areas were reviewed for macOS. First is macOS supports authentication via a smart card (Configuring MacOS for Smart Card–Only Authentication, n.d.). Second is macOS supports integration with Apple identities. This allows the operating system to leverage strong authentication features from that identity.
iOS: iOS is noted as supporting both knowledge and inherence-based authentication as part of the core operating system. Availability of inherence-based authentication is limited to sensors built into the device (i.e., fingerprint reader). Possession based authentication is possible using third party security keys (“YubiKey For Mobile Devices,” n.d.). Second is iOS supports integration with Apple identities. This allows the operating system to leverage strong authentication features from that identity.
Android: Android is noted as supporting both knowledge and inherence-based authentication (Kunda et al., 2018) as part of the core operating system. Availability of inherence-based authentication is limited to sensors built into the device (i.e., fingerprint reader). Possession based authentication is possible using third party security keys (“YubiKey For Mobile Devices,” n.d.). Android also allows for using a Google identity to sign into the device.
Learnings Taken from the Adoption of Strong Authentication
From the case studies and research identified several learnings can be noted regarding the adoption of strong authentication.
There needs to be a clear mandate for implementation. This can either be required by regulation (Sinigaglia et al., 2020), recommended by industry or government bodies (Cyber Essentials | CISA, n.d.) (Essential Eight Explained | Cyber.Gov.Au, n.d.) or done to manage business risk (Colnago et al., 2018). For a change to succeed it must have a clear mandate and drive to occur.
Users need to be convinced as the need for change (Ackerman, 2017). Regular reinforcement is then needed to maintain momentum (Colnago et al., 2018). Without convincing users to adopt new practices the goal of any implementation will not succeed.
Solution implemented must be usable. To achieve this it needs to be as close to effortless for users to consume (Bonneau et al., 2012). Where authentication provides too much of an impediment (Schaffer, 2019) users will find ways to bypass it. The entire user base needs to be considered in the design of the solution. What may be suitable to one generation (Ackerman, 2017) may not to others (Das et al., 2019).
The strong authentication solution must consider wider context and process in which it will be used. How users onboard, consume and offboard from the solution must be planned (Colnago et al., 2018). Corner cases need to be addressed – for example how do user with a several token authenticate against a kiosk (Lyastani et al., 2020, p. 2)? Finally, ways to address issues with the process need to be in place. For example how does a user recover from loss of a credential (Bonneau et al., 2012)?
Lastly the solution needs to be implemented well. Users will have low tolerance for anything which disrupts their regular work. Initial issues in the implementation of an authentication system can generate long term perception issues which are difficult to address.
Discussion
While not exhaustive, two gaps are noted in the research reviewed. First is lack of recent unbiased material covering formal validation and proof supporting authentication mechanisms and systems. This is needed to provide clarity on the usability, efficiency and effectiveness of those mechanisms and systems. Given changes in threats over time the material needs to be refreshed periodically. Second is an incomplete view around the drivers, approaches and outcomes from deployment of strong authentication systems. This is needed to give stakeholders an unbiased view on what a ‘good’ deployment of strong authentication looks like.
Authentication Concepts
Three key components can be taken as part of a strong authentication definition. First is authentication must be usable. Users will either not adopt or find ways to circumvent authentication they find difficult to use. For an authentication system to be accepted its use must be as close to effortless as possible.
Second is authentication must be tailored to situations. For example, Users on a phone will struggle to enter a 14-character password, users on a computer will struggle to use a fingerprint or smartcard without matching technology. Tailoring must also consider lifecycle of the authentication process. Users will forget and lose authentication material – ways to recover from this must be in place.
Third is the authentication system must be resistant to attack. Subverting an authentication system allows an attacker to assume the identity of a target. Preventing this from happening is key in maintaining a secure system.
From these components interesting observations can be taken. Multi-factor authentication is not a must – providing a system is sufficiently resilient to attack it is not required to overburden a user with unneeded complexity. Authentication needs to be periodically revisited. Situations and attacks change over time – authentication needs to match this.
Market Review of Strong authentication offerings
Review of Top 25 Websites
Of the twenty-three identities used across the top twenty-five websites nine identities do not make any form of multi factor authentication available.
Of those nine identities five support signing in using alternative identities which do support multi factor authentication. Availability of identity providers can simplify implementing a strong authentication scheme for a website. Instead of having to develop and maintain the capability from scratch, sites can leverage market leading identity providers. Trade-offs in doing this require further analysis.
Two out of the remaining four sites with no MFA support (seek.com.au & MyServiceNSW) contain personally sensitive information. It is interesting to note these websites did not judge the risk of account compromise to be worth the effort of implementing stronger authentication.
Of the multi factor technologies available text message is the most frequently supported (in twelve of twenty-three identities). Following that is authenticator applications (nine out of twenty-three identities). This is expected due to these being the oldest of the options available. Application or device prompt is the third most available technology. This is limited to providers which have their own mobile applications and the ability to leverage those.
Last is the support available for security keys. Websites analysed had a higher proportion of FIDO2 use. This could point to it either being easier to implement and/or the FIDO alliance learning lessons from the initial rollout of U2F.
Review of popular operating systems
All operating systems listed have varying level of support for strong authentication options. Operating systems are increasingly becoming linked with web-based identities. This allows for those systems to leverage additional levels of protection associated with that identity.
Learnings Taken from the Adoption of Strong Authentication
A review of available literature identified limited case studies on the deployment of strong authentication. To draw better conclusions more details of the rollouts are needed. Lessons from adoption do follow those around core authentication concepts.
To be accepted solutions must be usable, tailored to the target situation and people must see the benefits of it. Without this these will be resistance to adoption.
Given the proliferation of sites people use leveraging standards-based authentication approaches can also assist here. Forcing a user to utilise multiple multi-factor authentication options will adversely affect usability.
Conclusion
From a review of material, several conclusions can be drawn.
First is secure authentication can be regarded as a system which is usable, tailored to support required processes and resistant to attacks. Authentication needs to be considered as part of an existing process. Due to this it needs to change as situations and attacks progress. Drive towards FIDO2 and password less authentication is seen as a considerable advantage here.
Second is that moving towards standards-based authentication is of considerable value to the ecosystem. Propriety authentication systems can be difficult to assess and validate. They can also be difficult to integrate with larger solutions and support a supplier ecosystem. Involvement of multi key vendors in initiatives like FIDO2 is seen as a strong point here.
Third is that implementing a robust feature rich authentication system is hard. To address this changing some of the existing thinking may be required. Instead of building everything inhouse, leveraging third party identity providers may be an option.
Last in that suppliers have a key role to play in further driving the adoption of strong authentication. Instead of making additional authentication yet another setting, suppliers can work to educate their customers of the risks available and the ease in mitigating them.
One area is noted as requiring more research. This is looking at review of strong authentication system adoption by users and organisations. Doing this will allow for more lessons to be captured and shared back with the ecosystem overall. This in turn can be used to drive faster adoption of strong authentication.
References
- Ackerman, P. (2017). Impediments to Adoption of Two-factor Authentication by Home End-Users. 23.
- Agrawal, H. (2020, July 8). How Hackers Hack Your Accounts Password & Ways To Avoid Being Hacked. ShoutMeTech. https://shoutmetech.com/how-hackers-hack/
- Alexa—Top sites. (n.d.). Retrieved December 6, 2020, from https://www.alexa.com/topsites
- Arias-Cabarcos, P., Krupitzer, C., & Becker, C. (2019). A Survey on Adaptive Authentication. ACM Computing Surveys, 52(4), 80:1-80:30. https://doi.org/10.1145/3336117
- Blonder, G. E., Greenspan, S. L., Mirville, J. R., & Sugla, B. (1998). Transaction authorization and alert system (Patent No. US5708422A).
- Bonneau, J., Herley, C., Oorschot, P. C. v, & Stajano, F. (2012). The Quest to Replace Passwords: A Framework for Comparative Evaluation of Web Authentication Schemes. 2012 IEEE Symposium on Security and Privacy, 553–567. https://doi.org/10.1109/SP.2012.44
- Colnago, J., Devlin, S., Oates, M., Swoopes, C., Bauer, L., Cranor, L., & Christin, N. (2018). “It’s not actually that horrible”: Exploring Adoption of Two-Factor Authentication at a University. Proceedings of the 2018 CHI Conference on Human Factors in Computing Systems, 1–11. https://doi.org/10.1145/3173574.3174030
- Configuring macOS for smart card–only authentication. (n.d.). Apple Support. Retrieved January 23, 2021, from https://support.apple.com/en-au/guide/deployment-reference-macos/apdd3d1cd57d/1/web/1
- Cyber Essentials | CISA. (n.d.). Retrieved December 12, 2020, from https://www.cisa.gov/cyber-essentials
- Das, S., Streiff, J., Huber, L. L., & Camp, L. J. (2019). WHY DON’T ELDERS ADOPT TWO-FACTOR AUTHENTICATION? BECAUSE THEY ARE EXCLUDED BY DESIGN. Innovation in Aging, 3(Supplement_1), S325–S326. https://doi.org/10.1093/geroni/igz038.1186
- Dasgupta, D., Roy, A., & Nag, A. (2017). Advances in User Authentication (1st ed. 2017 edition). Springer.
- De Cristofaro, E., Du, H., Freudiger, J., & Norcie, G. (2013). A comparative usability study of two-factor authentication. ArXiv Preprint ArXiv:1309.5344.
- Essential Eight Explained | Cyber.gov.au. (n.d.). Retrieved December 12, 2020, from https://www.cyber.gov.au/acsc/view-all-content/publications/essential-eight-explained
- FIDO Alliance. (2020). FIDO2: Web Authentication (WebAuthn). FIDO Alliance. https://fidoalliance.org/fido2/fido2-web-authentication-webauthn/
- Frazier, S. (2019, December 9). The 2019 State of the Auth Report: Has 2FA Hit Mainstream Yet? Duo Security. https://duo.com/blog/the-2019-state-of-the-auth-report-has-2fa-hit-mainstream-yet
- Giandomenico, A. (2017, June 27). Know Your Enemy: Understanding Threat Actors. CSO Online. https://www.csoonline.com/article/3203804/know-your-enemy-understanding-threat-actors.html
- Gupta, C. (2017). The Market’s Law of Privacy: Case Studies in Privacy/Security Adoption. Washington and Lee Law Review Online, 73(2), 756.
- Henricks, A., & Kettani, H. (2019). On Data Protection Using Multi-Factor Authentication. Proceedings of the 2019 International Conference on Information System and System Management, 1–4. https://doi.org/10.1145/3394788.3394789
- Kunda, D., Link to external site, this link will open in a new window, & Chishimba, M. (2018). A Survey of Android Mobile Phone Authentication Schemes. Mobile Networks and Applications; New York, 1–9. http://dx.doi.org.ezproxy.csu.edu.au/10.1007/s11036-018-1099-7
- Lyastani, S. G., Schilling, M., Neumayr, M., Backes, M., & Bugiel, S. (2020). Is FIDO2 the Kingslayer of User Authentication? A Comparative Usability Study of FIDO2 Passwordless Authentication. 2020 IEEE Symposium on Security and Privacy (SP), 268–285. https://doi.org/10.1109/SP40000.2020.00047
- Manning, R. (2020, February 19). 2020 State of Password and Authentication Report | YubiKey. Yubico. https://www.yubico.com/blog/yubico-releases-2020-state-of-password-and-authentication-security-behaviors-report/
- Microsoft. (2020). Implementing strong user authentication with Windows Hello for Business. IT Showcase. https://www.microsoft.com/en-us/itshowcase/implementing-strong-user-authentication-with-windows-hello-for-business
- M’Raihi, D., Bellare, M., Hoornaert, F., Naccache, D., & Ranen, O. (2005, December). RFC4226—HMAC-based One-time Password algorithm. https://www.ietf.org/rfc/rfc4226.txt
- Rocha, R., Carneiro, D., & Novais, P. (2021). Continuous authentication with a focus on explainability. Neurocomputing, 423, 697–702. https://doi.org/10.1016/j.neucom.2020.02.122
- Schaffer, K. (2019). Rethinking Authentication. IT Professional, 21(6), 52–55. https://doi.org/10.1109/MITP.2019.2942792
- Shah, S. W., & Kanhere, S. S. (2019). Recent Trends in User Authentication – A Survey. IEEE Access, 7, 112505–112519. https://doi.org/10.1109/ACCESS.2019.2932400
- Sinigaglia, F., Carbone, R., Costa, G., & Zannone, N. (2020). A survey on multi-factor authentication for online banking in the wild. Computers & Security, 95, 101745. https://doi.org/10.1016/j.cose.2020.101745
- The Breaches Multifactor Authentication Could Have Prevented | tyntec. (n.d.). Retrieved December 12, 2020, from https://www.tyntec.com/blog/breaches-multifactor-authentication-could-have-prevented
- Theofanos, M. (2020). Is Usable Security an Oxymoron? Computer, 53(2), 71–74. https://doi.org/10.1109/MC.2019.2954075
- Verizon. (2020). 2020 Data Breach Investigations Report. https://enterprise.verizon.com/resources/reports/2020-data-breach-investigations-report.pdf
- Wang, C., Wang, Y., Chen, Y., Liu, H., & Liu, J. (2020). User authentication on mobile devices: Approaches, threats and trends. Computer Networks, 170, 107118. https://doi.org/10.1016/j.comnet.2020.107118
- Wiefling, S., Dürmuth, M., & Lo Iacono, L. (2020). More Than Just Good Passwords? A Study on Usability and Security Perceptions of Risk-based Authentication. Annual Computer Security Applications Conference, 203–218. https://doi.org/10.1145/3427228.3427243
- YubiKey For Mobile Devices. (n.d.). Yubico. Retrieved January 23, 2021, from https://www.yubico.com/products/yubikey-for-mobile/